IS-IS is a link-state interior gateway routing protocol. Like OSPF, IS-IS runs the Dijkstra shortest-path first (SPF) algorithm to create a database of the network’s topology and, from that database, to determine the best (that is, shortest) path to a destination.
 |
| IS-IS : Intermediate System to Intermediate System |
IS-IS as Intermediate System to Intermediate System
Unlike OSPF, which was developed and standardized by the Internet Engineering Task Force (IETF), IS-IS is an ANSI ISO protocol and was originally based on the Digital Equipment Corporation DECNET Phase V Network Technology.
IS-IS uses a slightly different terminology than OSPF for naming its protocol packets. The packets that IS-IS routers send to each other describing the network topology are called link-state protocol data units (link-state PDUs, or LSPs). In addition to describing the network topology that the router knows about, the link-state PDUs include IP routes, checksums, and other information.
Similar to OSPF, all IS-IS routers place the information in the received link-stated PDUs into their link-state database, and all routers have the same view of the network’s topology. IS-IS runs the SPF algorithm on the information in the link-state database to determine the shortest path to each destination on the network, placing the destination/next-hop pairs that result from the SPF calculation into the IS-IS routing database.
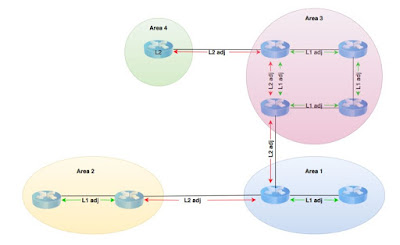
Unlike other IP routing protocols, which typically run on TCP, UDP, or IP, which are OSI Layer 3 or Layer 4 protocols, IS-IS runs directly on the data link layer (Layer 2).
As a result, an interface that runs IS-IS doesn’t need an IP address to exchange IS-IS information, and you don’t need to configure an inet family on interfaces running IS-IS. Instead, only the router needs an IP address, which makes the router configuration simpler (but not necessarily better).
Because it was developed as part of the OSI network protocols and not part of TCP/IP, IS-IS doesn’t use IP addresses. IS-IS addresses are called NETs, or network entity titles. While IP addresses are 32 bits long and are normally written in dotted quad notation (such as 192.168.1.2), NETs can be 8 to 20 bytes long, but are generally 10 bytes long and are written as shown in this example:
49.0001.1921.6800.1002.00
The IS-IS address consists of three parts:
Area identifier:
The first three bytes are the area ID. The first byte of this example — 49 — is the address family identifier (AFI) of the authority, which is equivalent to the IP address space that is assigned to an autonomous system. The AFI value 49 is what IS-IS uses for private addressing, which is the equivalent of RFC 1918 address space for IP protocols.
The second two bytes of the area ID — 0001 — represent the IS-IS area number. In this example, the area number is 1.
System identifier:
The next six bytes identify the node (that is, the router) on the network. The system identifier is equivalent to the host or address portion on an IP address.Although you can choose any value for the system identifier, a commonly used method is to use binary-coded decimal (BCD) which involves taking the router’s IP address (the address you assigned to the lo0 loopback interface), filling in all leading zeros, and then repositioning the decimal points to form three two-byte numbers.
In this example, if you pad the IP address 192.168.1.2 with zeros, the result is 192.168.001.002. Rearranging the decimal points gives you 1921.6800.1002.
NET selector:
The final two bytes are the NET selector (NSEL). For IS-IS, they must always be 00, to indicate “this system.”
Comments
Post a Comment