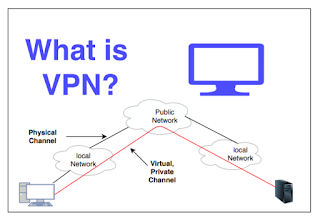
Virtual Private Network is a connection method used to add security and privacy to private and public networks. For instance, like WiFi Hotspots and the Internet. Corporations use Virtual Private Networks to protect sensitive data. However, using a personal VPN is increasingly becoming more popular as more interactions that were previously face-to-face transition to the Internet. Increase privacy with a Virtual Private Network because the user's initial IP address replaced with one from the Virtual Private Network provider. Subscribers can obtain an IP address from any gateway city the VPN service provides. For instance, you may live in San Francisco, but with a Virtual Private Network, you can appear to live in Amsterdam, New York, or any number of gateway cities.
Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more.
These days VPNs are really popular, but not for the reasons they were originally created. They originally were just a way to connect business networks together securely over the internet or allow you to access a business network from home.
VPNs essentially forward all your network traffic to the network, which is where the benefits – like accessing local network resources remotely and bypassing Internet censorship – all come from. Most operating systems have integrated VPN support.
- Hide IP Address:
Connecting to a virtual Private Network often conceals your real IP address. - Change IP address:
Using a VPN is almost certainly result in getting a different IP address. - Encrypt Data Transfers:
A Virtual Private Network will protect the data you transfer over public WiFi. - Mask your Location:
Using an VPN users can choose the country of region for their internet connection. - Access Blocked Websites:
Access blocked Websites using VPN.
Protocols of Virtual Private Network
The number of protocols and available security features continue to grow with time. The most common protocols are:
PPTP: PPTP has been around since the days of Windows 95. The main selling point of PPTP is that it can be simply setup on every major OS. In short, PPTP tunnels a point-to-point connection over the GRE protocol. Unfortunately, the PPTP protocol security called into question in recent years. It is still strong, but not the most secure.
L2TP/IPsec: L2TP over IPsec is more secure than PPTP and offers more features. L2TP/IPsec is a way of implementing two protocols together in order to gain the best features of each. For example, the L2TP protocol used to create a tunnel and IPsec provides a secure channel. These measures make for an impressively secure package.
Open VPN: OpenVPN is an SSL-based Virtual Private Network that continues to gain popularity. The software used is open source and freely available. SSL is a mature encryption protocol, and OpenVPN can run on a single UDP or TCP port, making it extremely flexible.
How Does VPN works?
When you connect your computer (or another device, such as a smartphone or tablet) to a VPN, the computer acts as if it’s on the same local network as the VPN. All your network traffic is sent over a secure connection to the VPN. Because your computer behaves as if it’s on the network, this allows you to securely access local network resources even when you’re on the other side of the world. You’ll also be able to use the Internet as if you were present at the VPN’s location, which has some benefits if you’re using pubic Wi-Fi or want to access geo-blocked websites.
When you browse the web while connected to a VPN, your computer contacts the website through the encrypted VPN connection. The VPN forwards the request for you and forwards the response from the website back through the secure connection. If you’re using a USA-based VPN to access Netflix, Netflix will see your connection as coming from within the USA.
Hello, an amazing Information dude. Thanks for sharing this nice information with us. Best Firestick vpn service uk
ReplyDeleteThank you very much Glenn,
DeleteKeep reading.
Regards,
Netwyman