AAA refers to Authentication, Authorization and Accounting. It is used to refer to a family of protocols that mediate network access. Two network protocols providing this functionality are particularly popular: the RADIUS protocol, and its newer Diameter counterpart.
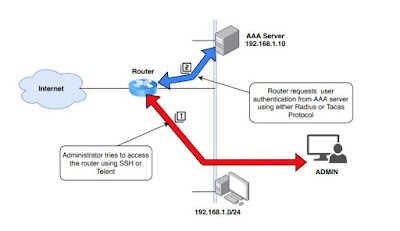
The administrator can take an access to a router or a device through console but it is very inconvenient if someone is sitting far from the place of that devices, so eventually he has to take remote access to that device.
But as the remote access will be available by using an IP address therefore it is possible that an unauthorized user can take access using that same IP address therefore for security measures, we have to put authentication. Also, the packets exchange between the devices should be encrypted so that any other person should not be able to capture that sensitive information. Therefore, a framework called AAA is used to provide that extra level of security.
The administrator can take an access to a router or a device through console but it is very inconvenient if someone is sitting far from the place of that devices, so eventually he has to take remote access to that device.
But as the remote access will be available by using an IP address therefore it is possible that an unauthorized user can take access using that same IP address therefore for security measures, we have to put authentication. Also, the packets exchange between the devices should be encrypted so that any other person should not be able to capture that sensitive information. Therefore, a framework called AAA is used to provide that extra level of security.
 |
| AAA Authentication |
Authentication:
Process by which it can be identified that the user, which want to access the network resources, valid or not by asking some credentials such as username and password. Common methods are to put authentication on console port, AUX port or vty lines.
As a network administrator, we can control how a user is authenticated if someone wants to access the network. Some of these methods include using the local database of that device (router) or sending authentication request to an external server like ACS server. To specify the method to be used for authentication, default or customized authentication method list are used.
Authorization:
It provide capabilities to enforce policies on network resources after the user has gain access to the network resources through authentication. After the authentication is successful, authorization can be used to determine that what resources is the user allowed to access and the operations that can be performed.
Accounting:
It provide means of monitoring and capturing the events done by the user while accessing the network resources.It even monitors how long the user has an access to the network. The administrator can create an accounting method list to specify what should be accounted and to whom the accounting records should be send.
AAA Implementation:
AAA can be implemented by using the local database of the device or by using an external ACS server.
Local Database:
The local running configuration of the router or switch to implement AAA, we should create users first for authentication and provide privilege levels to user for Authorization.
ACS Server:
This is the common method used. An external ACS server is used (can be ACS device or software installed on Vmware) for AAA on which configuration on both router and ACS required. The configuration include creating user, separate customized method list for authentication, Authorization and Accounting.
The client or Network Access Server (NAS) sends authentication request to ACS server and the server takes the decision to allow the user to access the network resource or not according to the credentials provided by the user.
If the ACS server fails to authenticate, the administrator should mention to use the local database of the device as backup, in the method list, to implement AAA.
Examples of AAA protocols:
Terminal Access Controller Access-Control System (TACACS)
Diameter, a successor to Remote Authentication Dial-In User Service (RADIUS)
Terminal Access Controller Access-Control System Plus (TACACS+) a proprietary Cisco Systems protocol that provides access for network servers, routers and other network computing devices.
Types of AAA servers:
Home AAA (H-AAA)
Access Network AAA (AN-AAA) which communicates with radio network controllers
Broker AAA (B-AAA), which manages traffic between roaming partner networks
Configure these commands on the device in global configuration mode:
aaa new-model
aaa authentication login default local group tacacs+
Here the AAA method list is applied on all login attempts on all lines of the device, where first local database is checked and then if required, Terminal Access Controller Access Control System (TACACS) server is tried.
username cisco privilege 15 password 0 cisco
tacacs-server host 10.20.220.141
tacacs-server key cisco
Enable Debug TACACS and Debug AAA Authentication on the device under test.
NB#show debug
General OS:
TACACS access control debugging is on
AAA Authentication debugging is on
Perform a telnet on the device:
NB#show ip interface brief | exclude unassigned
NB#telnet 192.168.1.2
Trying 192.168.1.2 ... Open
User Access Verification
Username: cisco
*May 15 09:38:37.023: AAA/BIND(0000001E): Bind i/f
*May 15 09:38:37.023: AAA/AUTHEN/LOGIN (0000001E): Pick method list 'default'
Password:
NB>
You notice that it did not try to reach the TACACS server as username cisco was found locally.
Now, if you try to use a credential that is not configured locally on the box:
NB#telnet 192.168.1.2
Trying 192.168.1.2 ... Open
User Access Verification Username:
* May 15 09:40:01.099: AAA/BIND (0000001F): Bind i/f
* May 15 09:40:01.099: AAA/AUTHEN/LOGIN (0000001F): Pick method list 'default'
Username: cisco1
*May 15 09:40:11.095: TPLUS: Queuing AAA Authentication request 31 for processing
*May 15 09:40:11.095: TPLUS: processing authentication start request id 31
* May 15 09:40:11.095: TPLUS: Authentication start packet created for 31(cisco1)
* May 15 09:40:11.095: TPLUS: Using server 10.20.220.141
* May 15 09:40:11.095: TPLUS(0000001F)/0/NB_WAIT/47A14C34: Started 5 sec timeout
* May 15 09:40:16.095: TPLUS(0000001F)/0/NB_WAIT/47A14C34: timed out
* May 15 09:40:16.095: TPLUS(0000001F)/0/NB_WAIT/47A14C34: timed out, clean up
* May 15 09:40:16.095: TPLUS(0000001F)/0/47A14C34: Processing the reply packet
% Authentication failed
You notice that it tries to reach the TACACS server 10.20.220.141. It is an expected default behavior. There is no username cisco1 configured on the TACACS server, hence shows Authentication failed.
If the device has AAA Authentication login default group tacacs+ local in the configuration, its first preference is TACACS. If the TACACS is reachable, but no user has configured on it, it will not fall back and try to search in the local database. It will display% Authentication failed message.
Process by which it can be identified that the user, which want to access the network resources, valid or not by asking some credentials such as username and password. Common methods are to put authentication on console port, AUX port or vty lines.
As a network administrator, we can control how a user is authenticated if someone wants to access the network. Some of these methods include using the local database of that device (router) or sending authentication request to an external server like ACS server. To specify the method to be used for authentication, default or customized authentication method list are used.
Authorization:
It provide capabilities to enforce policies on network resources after the user has gain access to the network resources through authentication. After the authentication is successful, authorization can be used to determine that what resources is the user allowed to access and the operations that can be performed.
Accounting:
It provide means of monitoring and capturing the events done by the user while accessing the network resources.It even monitors how long the user has an access to the network. The administrator can create an accounting method list to specify what should be accounted and to whom the accounting records should be send.
AAA Implementation:
AAA can be implemented by using the local database of the device or by using an external ACS server.
Local Database:
The local running configuration of the router or switch to implement AAA, we should create users first for authentication and provide privilege levels to user for Authorization.
ACS Server:
This is the common method used. An external ACS server is used (can be ACS device or software installed on Vmware) for AAA on which configuration on both router and ACS required. The configuration include creating user, separate customized method list for authentication, Authorization and Accounting.
The client or Network Access Server (NAS) sends authentication request to ACS server and the server takes the decision to allow the user to access the network resource or not according to the credentials provided by the user.
If the ACS server fails to authenticate, the administrator should mention to use the local database of the device as backup, in the method list, to implement AAA.
Examples of AAA protocols:
Terminal Access Controller Access-Control System (TACACS)
Diameter, a successor to Remote Authentication Dial-In User Service (RADIUS)
Terminal Access Controller Access-Control System Plus (TACACS+) a proprietary Cisco Systems protocol that provides access for network servers, routers and other network computing devices.
Types of AAA servers:
Home AAA (H-AAA)
Access Network AAA (AN-AAA) which communicates with radio network controllers
Broker AAA (B-AAA), which manages traffic between roaming partner networks
Configure these commands on the device in global configuration mode:
aaa new-model
aaa authentication login default local group tacacs+
Here the AAA method list is applied on all login attempts on all lines of the device, where first local database is checked and then if required, Terminal Access Controller Access Control System (TACACS) server is tried.
username cisco privilege 15 password 0 cisco
tacacs-server host 10.20.220.141
tacacs-server key cisco
Enable Debug TACACS and Debug AAA Authentication on the device under test.
NB#show debug
General OS:
TACACS access control debugging is on
AAA Authentication debugging is on
Perform a telnet on the device:
NB#show ip interface brief | exclude unassigned
|
Interface
|
IP-Address
|
OK?
|
Method
|
Status
|
Protocol
|
|
FastEthernet0/1
|
10.197.235.96
|
YES
|
DHCP
|
Up
|
Up
|
|
Loopback0
|
192.168.1.2
|
YES
|
Manual
|
Up
|
Up
|
NB#telnet 192.168.1.2
Trying 192.168.1.2 ... Open
User Access Verification
Username: cisco
*May 15 09:38:37.023: AAA/BIND(0000001E): Bind i/f
*May 15 09:38:37.023: AAA/AUTHEN/LOGIN (0000001E): Pick method list 'default'
Password:
NB>
You notice that it did not try to reach the TACACS server as username cisco was found locally.
Now, if you try to use a credential that is not configured locally on the box:
NB#telnet 192.168.1.2
Trying 192.168.1.2 ... Open
User Access Verification Username:
* May 15 09:40:01.099: AAA/BIND (0000001F): Bind i/f
* May 15 09:40:01.099: AAA/AUTHEN/LOGIN (0000001F): Pick method list 'default'
Username: cisco1
*May 15 09:40:11.095: TPLUS: Queuing AAA Authentication request 31 for processing
*May 15 09:40:11.095: TPLUS: processing authentication start request id 31
* May 15 09:40:11.095: TPLUS: Authentication start packet created for 31(cisco1)
* May 15 09:40:11.095: TPLUS: Using server 10.20.220.141
* May 15 09:40:11.095: TPLUS(0000001F)/0/NB_WAIT/47A14C34: Started 5 sec timeout
* May 15 09:40:16.095: TPLUS(0000001F)/0/NB_WAIT/47A14C34: timed out
* May 15 09:40:16.095: TPLUS(0000001F)/0/NB_WAIT/47A14C34: timed out, clean up
* May 15 09:40:16.095: TPLUS(0000001F)/0/47A14C34: Processing the reply packet
% Authentication failed
You notice that it tries to reach the TACACS server 10.20.220.141. It is an expected default behavior. There is no username cisco1 configured on the TACACS server, hence shows Authentication failed.
If the device has AAA Authentication login default group tacacs+ local in the configuration, its first preference is TACACS. If the TACACS is reachable, but no user has configured on it, it will not fall back and try to search in the local database. It will display% Authentication failed message.
Comments
Post a Comment