VRF lite is one types of wait wait before start understainding of VRF lite you guys should be aware of PE as well as CE Router. in MPLS networks related scenario the PE router is the Provider's edge router and the CE is the Customer edge router where the routing or L2 protocol works. The MPLS works start between one end PE to other end PE routers.
What is VRF lite?
VRFs as VPN Routing and Forwarding instances, are most commonly associated with MPLS service providers. In such networks, MPLS encapsulation is used to isolate individual customers' traffic and an independent routing table (VRF) is maintained for each customer. Mostly the MP-BGP is employed to facilitate complex redistribution schemes to import and export routes to and from VRFs to provide Internet connectivity.
VRF-lite is a feature in MPLS environment that enables a service provider to support two or more VPNs, where IP addresses can be overlapped among the VPNs. VRF-lite uses input interfaces to distinguish routes for different VPNs and forms virtual packet-forwarding tables by associating one or more Layer 3 interfaces with each VRF.
Interfaces in a VRF can be either physical, such as Ethernet ports, or logical, such as VLAN SVIs, but a Layer 3 interface cannot belong to more than one VRF at any time.
VRF configuration isn't at all dependent on MPLS (the two components just work well together). In Cisco terminology, deployment of VRFs without MPLS is known as VRF lite, and this article discusses a scenario where such a solution could come in handy
In which scenario admin will use VRF lite PE routers or CE routers?
Here I am talking about the PE - Provider edge routers exchange routing information with CE devices by using static routing or a routing protocol such as BGP, RIPv1, or RIPv2.
Customer edge (CE) devices provide customer access to the service provider network over a data link to one or more provider edge routers. The CE device advertises the site's local routes to the provider edge router and learns the remote VPN routes from it.
The reason to use PE routers in VRF lite scenarios :
The reason of the PE device is to only required to maintain VPN routes for those VPNs to which it is directly attached, eliminating the need for the PE to maintain all of the service provider VPN routes. Each PE router maintains a VRF for each of its directly connected sites. Multiple interfaces on a PE router can be associated with a single VRF if all of these sites participate in the same VPN.
Each VPN is mapped to a specified VRF. After learning local VPN routes from CEs, a PE router exchanges VPN routing information with other PE routers by using internal BGP (IBPG).
With VRF-lite, multiple customers can share one CE, and only one physical link is used between the CE and the PE. The shared CE maintains separate VRF tables for each customer and switches or routes packets for each customer based on its own routing table. VRF-lite extends limited PE functionality to a CE device, giving it the ability to maintain separate VRF tables to extend the privacy and security of a VPN to the branch office.
Prerequisites for MPLS Multi-VRF
The network's core and provider edge routers must be properly configured for MPLS VPN operation.
Multi-VRF is a feature that enables a service provider to support two or more VPNs, where IP addresses can be overlapped among the VPNs. Multi-VRF uses input interfaces to distinguish routes for different VPNs, and forms virtual packet-forwarding tables by associating one or more Layer 3 interfaces with each VRF. Interfaces in a VRF can be either physical, such as Ethernet ports, or logical, such as VLAN SVIs (Switched Virtual Interfaces), but a Layer 3 interface cannot belong to more than one VRF at any one time. The Multi-VRF feature thus allows an operator to support two or more routing domains on a CE router, with each routing domain having its own set of interfaces and its own set of routing and forwarding tables. MPLS Multi-VRF makes it possible to extend the Label Switched Paths (LSPs) to the CE and into each routing domain that the CE supports.
Companents of VRF lite
VPN route target communities:
The first one is VPN route target community and it consists of lists of all other members of a VPN community. You need to configure VPN route targets for each VPN community member.
MP-BGP peering of VPN community PE routers:
The second is the MP-iBGP peering which will propagates VRF reachability information to all members of a VPN community. You need to configure BGP peering in all PE routers within a VPN community.
VPN forwarding:
The third one is VPN forwarding and it transports all traffic between all VPN community members across a VPN service-provider network.
Restrictions with MPLS Multi-VRF
Configuring PE-to-CE MPLS Forwarding and Signalling (when BGP is not the routing protocol)
If any protocol other than BGP is used for routing between the PE and the CE, LDP should be used to signal the labels on the PE and CE VRF interfaces, as shown here next.
SUMMARY STEPS
1. enable
enable
2. configure terminal
configure terminal
3. interface interface-id
interface interface-id
4. mpls ip
mpls ip
Configuring BGP PE-to-CE Routing Sessions
To configure a BGP PE-to-CE routing session, perform the task presented next on the CE and on the PE.
SUMMARY STEPS
1. enable
enable
2. configure terminal
configure terminal
3. router bgp autonomous-system-number
router bgp autonomous-system-number
4. network network-number mask network-mask
network network-number mask network-mask
5. redistribute ospf process-id match internal
redistribute ospf process-id match internal
6. network network-number area area-id
network network-number area area-id
7. address-family ipv4 vrf vrf-name
address-family ipv4 vrf vrf-name
8. neighbor {ip-address | peer-group-name} remote-as as-number
neighbor {ip-address | peer-group-name} remote-as as-number
9. neighbor address activate
neighbor address activate
What is VRF lite?
VRFs as VPN Routing and Forwarding instances, are most commonly associated with MPLS service providers. In such networks, MPLS encapsulation is used to isolate individual customers' traffic and an independent routing table (VRF) is maintained for each customer. Mostly the MP-BGP is employed to facilitate complex redistribution schemes to import and export routes to and from VRFs to provide Internet connectivity.
VRF-lite is a feature in MPLS environment that enables a service provider to support two or more VPNs, where IP addresses can be overlapped among the VPNs. VRF-lite uses input interfaces to distinguish routes for different VPNs and forms virtual packet-forwarding tables by associating one or more Layer 3 interfaces with each VRF.
Interfaces in a VRF can be either physical, such as Ethernet ports, or logical, such as VLAN SVIs, but a Layer 3 interface cannot belong to more than one VRF at any time.
VRF configuration isn't at all dependent on MPLS (the two components just work well together). In Cisco terminology, deployment of VRFs without MPLS is known as VRF lite, and this article discusses a scenario where such a solution could come in handy
In which scenario admin will use VRF lite PE routers or CE routers?
Here I am talking about the PE - Provider edge routers exchange routing information with CE devices by using static routing or a routing protocol such as BGP, RIPv1, or RIPv2.
Customer edge (CE) devices provide customer access to the service provider network over a data link to one or more provider edge routers. The CE device advertises the site's local routes to the provider edge router and learns the remote VPN routes from it.
The reason to use PE routers in VRF lite scenarios :
The reason of the PE device is to only required to maintain VPN routes for those VPNs to which it is directly attached, eliminating the need for the PE to maintain all of the service provider VPN routes. Each PE router maintains a VRF for each of its directly connected sites. Multiple interfaces on a PE router can be associated with a single VRF if all of these sites participate in the same VPN.
Each VPN is mapped to a specified VRF. After learning local VPN routes from CEs, a PE router exchanges VPN routing information with other PE routers by using internal BGP (IBPG).
With VRF-lite, multiple customers can share one CE, and only one physical link is used between the CE and the PE. The shared CE maintains separate VRF tables for each customer and switches or routes packets for each customer based on its own routing table. VRF-lite extends limited PE functionality to a CE device, giving it the ability to maintain separate VRF tables to extend the privacy and security of a VPN to the branch office.
Prerequisites for MPLS Multi-VRF
The network's core and provider edge routers must be properly configured for MPLS VPN operation.
Multi-VRF is a feature that enables a service provider to support two or more VPNs, where IP addresses can be overlapped among the VPNs. Multi-VRF uses input interfaces to distinguish routes for different VPNs, and forms virtual packet-forwarding tables by associating one or more Layer 3 interfaces with each VRF. Interfaces in a VRF can be either physical, such as Ethernet ports, or logical, such as VLAN SVIs (Switched Virtual Interfaces), but a Layer 3 interface cannot belong to more than one VRF at any one time. The Multi-VRF feature thus allows an operator to support two or more routing domains on a CE router, with each routing domain having its own set of interfaces and its own set of routing and forwarding tables. MPLS Multi-VRF makes it possible to extend the Label Switched Paths (LSPs) to the CE and into each routing domain that the CE supports.
Companents of VRF lite
VPN route target communities:
The first one is VPN route target community and it consists of lists of all other members of a VPN community. You need to configure VPN route targets for each VPN community member.
MP-BGP peering of VPN community PE routers:
The second is the MP-iBGP peering which will propagates VRF reachability information to all members of a VPN community. You need to configure BGP peering in all PE routers within a VPN community.
VPN forwarding:
The third one is VPN forwarding and it transports all traffic between all VPN community members across a VPN service-provider network.
Restrictions with MPLS Multi-VRF
- MPLS Multi-VRF can be configured only on Layer 3 interfaces.
- MPLS Multi-VRF is not supported by IGRP nor ISIS.
- Label distribution for a given VRF on a given router can be handled by either BGP or LDP, but not by both protocols.
- Multicast cannot operate on a Layer 3 interface already configured with MPLS Multi-VRF.
Configuring PE-to-CE MPLS Forwarding and Signalling (when BGP is not the routing protocol)
If any protocol other than BGP is used for routing between the PE and the CE, LDP should be used to signal the labels on the PE and CE VRF interfaces, as shown here next.
SUMMARY STEPS
1.
 enable
enable2.
 configure terminal
configure terminal3.
 interface interface-id
interface interface-id4.
 mpls ip
mpls ipConfiguring BGP PE-to-CE Routing Sessions
To configure a BGP PE-to-CE routing session, perform the task presented next on the CE and on the PE.
SUMMARY STEPS
1.
 enable
enable2.
 configure terminal
configure terminal3.
 router bgp autonomous-system-number
router bgp autonomous-system-number4.
 network network-number mask network-mask
network network-number mask network-mask5.
 redistribute ospf process-id match internal
redistribute ospf process-id match internal6.
 network network-number area area-id
network network-number area area-id7.
 address-family ipv4 vrf vrf-name
address-family ipv4 vrf vrf-name8.
 neighbor {ip-address | peer-group-name} remote-as as-number
neighbor {ip-address | peer-group-name} remote-as as-number9.
 neighbor address activate
neighbor address activate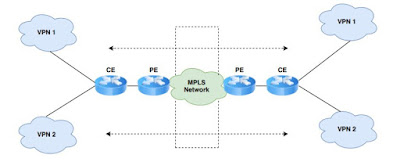
ulpasi-zo Alexis Thomas https://wakelet.com/wake/sCjSn_ezGwL2nF92iNRhn
ReplyDeletexinpytingscob
exodOrecpu Jayson Sandell Driver Easy Pro
ReplyDeleteThere
Yandex browser
fthehmuncakal